-
Solutions
Connectivity, Voice, & Collaboration
Network Connectivity Aggregation Services Managed Network Unified Communications (UCaaS) Contact Center (CCaaS) Microsoft Teams Direct Routing SIP Trunking Collaboration Services- Partners
- Why Netrio?
- Client Experience
- Resources
- Industries
- Contact Us
- 800-507-5770
Powerful Threat Detection and Incident Response for All Your Critical Infrastructure
CSP provides multiple essential security capabilities in a single SaaS solution, giving you everything you need for threat detection, incident response, and compliance management—all in a single pane of glass. CSP allows your organization to focus on proactively securing your assets while we provide notification of potential threats and malicious activity.
An elastic, cloud-based security solution, CSP can readily scale to meet your threat detection needs as your IT environment changes and grows.
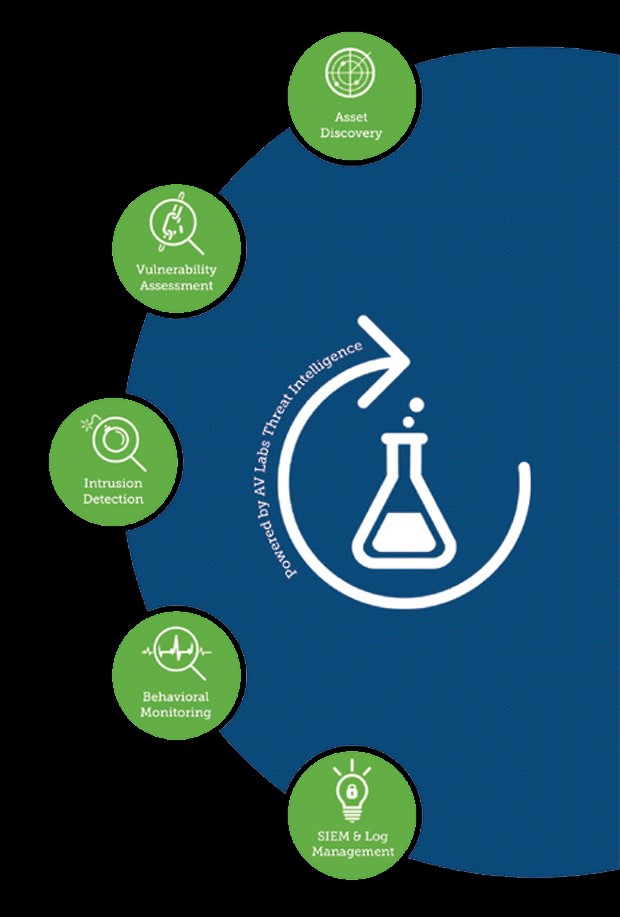
Asset Discovery
- API-powered asset discovery
- Network asset discovery
- Software and services discovery
Vulnerability Assessment
- Network vulnerability scanning
- Cloud vulnerability scanning
- Cloud infrastructure assessment
Intrusion Detection
- Cloud – Network – Host
- File Integrity Monitoring
Behavioral Monitoring
- Asset access logs
- Cloud access and activity logs (Azure Monitor, AWS: CloudTrail, CloudWatch, S3, ELB)
- AWS VPC Flow monitoring
- VMware ESXi access logs SIEM
SIEM & Log Management
- Event correlation
- Log management, with at least 12 months log retention
- Incident response
- Integrated threat intelligence from the AV Labs Security Team and the Open Threat Exchange (OTX)
AlienVault, AlienApp, AlienApps, AlienVault OSSIM, Open Threat Exchange, OTX, Unified Security Management, USM, USM Anywhere, USM Appliance, and USM Central, are trademarks of AlienVault and/or its affiliates. Other names may be trademarks of their respective owners.

“We sleep better at night knowing
Netrio is watching the network.”
— MIKE SHISKO | DIRECTOR IT | HITACHI CONSULTING
COMPANY
© 2025 Netrio, LLC. All Rights Reserved.

